Real-World Examples of Cyber Attacks
The 2017 Equifax Data Breach
-
Vulnerability Exploited: The attack exploited a vulnerability in Microsoft Windows, specifically a flaw in the SMB (Server Message Block) protocol. This vulnerability was known as "EternalBlue," which had been leaked from the NSA.
Mechanism: Once the ransomware infected a system, it encrypted files on the computer and demanded a ransom payment in Bitcoin to restore access.
Spread: The ransomware spread rapidly across networks due to its ability to propagate via the SMB protocol, affecting systems worldwide.
-
Scope: The attack had a global impact, affecting hundreds of thousands of computers across more than 150 countries.
Affected Organizations: It hit numerous organizations, including hospitals (such as the UK's National Health Service), government agencies, and businesses, leading to operational disruptions.
Financial Losses: The attack caused significant financial losses due to downtime, data recovery efforts, and ransom payments. The total estimated cost ran into hundreds of millions of dollars.
-
Immediate Response: Security researchers quickly identified a "kill switch" in the ransomware, which helped to slow its spread. The kill switch was a domain name that, when registered, halted further infections.
Long-Term Measures: Microsoft released patches for the vulnerable Windows versions, even those that were no longer officially supported, to protect against future attacks.
Policy and Awareness: The attack underscored the importance of cybersecurity practices, including timely software updates, robust backup strategies, and employee training to recognize phishing attempts and other threats.
WannaCry Ransomware Attack (2017)
-
Vulnerability Exploited: The attack took advantage of a vulnerability in Microsoft Windows, specifically targeting the SMB (Server Message Block) protocol. The exploit, known as "EternalBlue," was reportedly developed by the NSA and leaked by a hacking group.
Mechanism of Attack: WannaCry ransomware encrypted files on infected computers and demanded a ransom payment in Bitcoin to decrypt them. It used the exploit to spread to other vulnerable systems on the same network or across the internet.
Propagation: The ransomware was designed to spread automatically within networks and across the internet, leveraging the SMB vulnerability to infect additional computers rapidly.
-
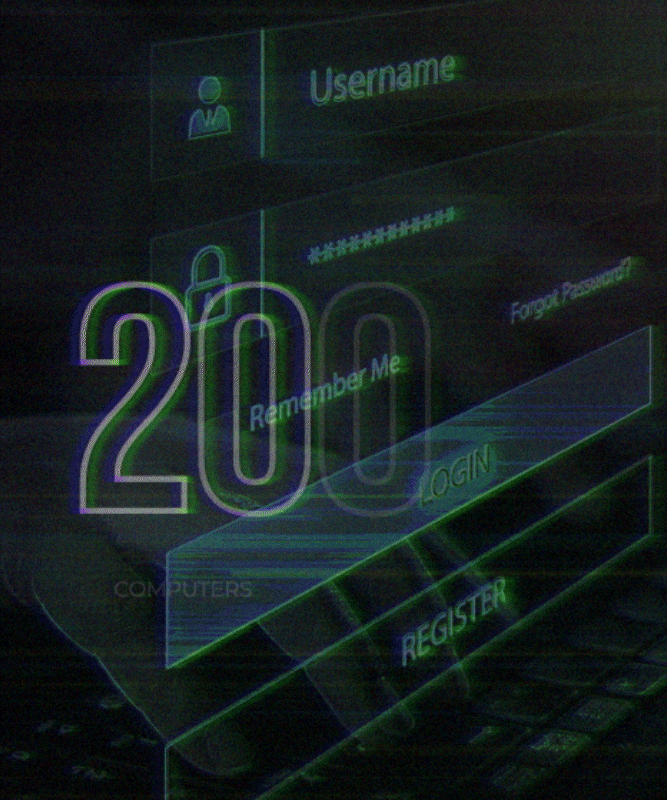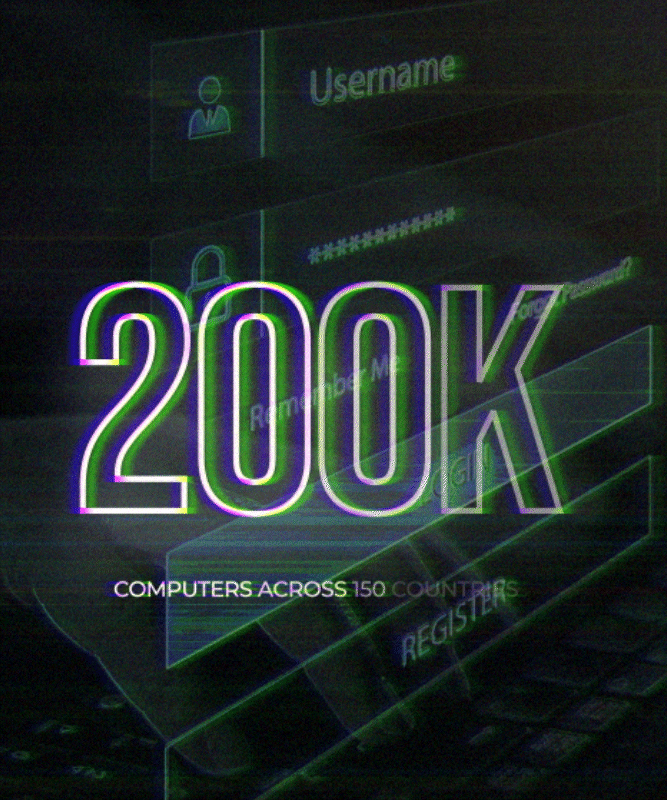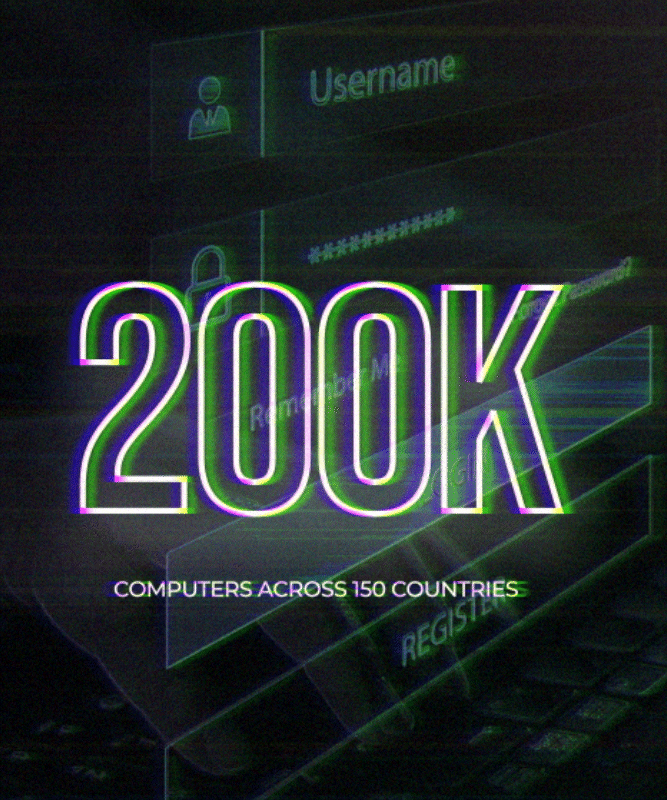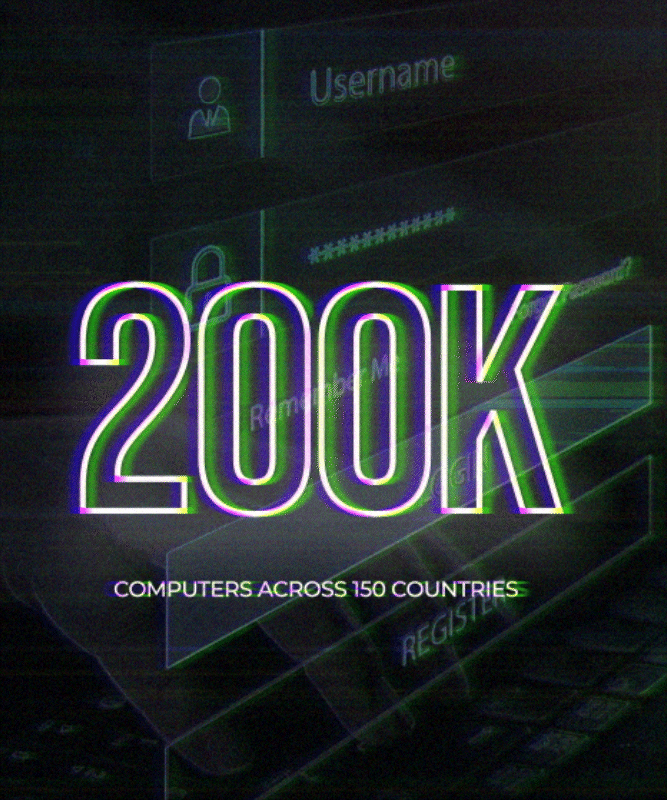
Global Reach: The attack affected over 200,000 computers in more than 150 countries, making it one of the most widespread ransomware incidents in history.
Affected Entities: Major organizations were hit, including hospitals (notably the UK's National Health Service), government agencies, and various businesses, causing significant operational disruptions.
Financial Consequences: The attack led to substantial financial losses due to downtime, data recovery efforts, and ransom payments. Estimates of the total economic impact run into hundreds of millions of dollars.
-
Immediate Actions: Security researchers identified a "kill switch" in the ransomware’s code, which was a domain name that, when registered, halted further infections. This discovery slowed the attack's spread significantly.
Patch Release: Microsoft responded by releasing emergency security patches for supported and unsupported versions of Windows to close the exploited vulnerability and prevent further infections.
Long-Term Measures: The incident emphasized the need for regular software updates, enhanced cybersecurity practices, and improved network security measures to protect against similar attacks in the future. It also highlighted the importance of incident response planning and backups.
SolarWinds Cyberattack (2020)
-
In 2020, the SolarWinds cyberattack targeted SolarWinds, an IT management software provider. The attackers embedded malicious code in a software update for SolarWinds' Orion platform.
Key Points:
Target: SolarWinds, a major IT software company.
Method: Malicious code hidden in a routine software update.
Spread: The update was distributed to SolarWinds' clients, including government agencies and corporations.
-
The breach had extensive effects on various organizations, causing operational disruptions and prompting security reviews.
Key Points:
Affected Groups: Multiple U.S. government agencies and major corporations.
Consequences: Significant operational disruptions and a major review of security practices.
Long-Term Effects: Led to comprehensive changes in security protocols and practices
-
Immediate Response: Security researchers quickly identified a "kill switch" in the ransomware, which helped to slow its spread. The kill switch was a domain name that, when registered, halted further infections.
Long-Term Measures: Microsoft released patches for the vulnerable Windows versions, even those that were no longer officially supported, to protect against future attacks.
Policy and Awareness: The attack underscored the importance of cybersecurity practices, including timely software updates, robust backup strategies, and employee training to recognize phishing attempts and other threats.